Last Updated May 23, 2011 07:59 PM
|
Other Reports
|
When Firefox was released late last year, there was a lot of excitement about the increased security and reliability of an open-source browser. People were tired of all the attacks against vulnerabilities in Microsoft's Internet Explorer (IE). Many switched to Firefox to reduce those problems, in addition to some new features of Firefox (like tabbed browsing -- which I have been using with IE and the NetCaptor add-in).
Others said that the reason that IE was being attacked was because it was such a large target. If a hacker is going to exploit problems, then they will look for the biggest target.
One the big vulnerabilities in IE is used by 'phishers' to obscure the address that you click on. The link looks like a valid site (like your bank), but clicking on the link takes to the phisher's site where they grab your financial information for fraudulent purposes. You experienced that with the message you received from "PayPal" Dec 20, 2004.
Many of these phishing techniques don't work in Firefox. But there is a new one that works in Firefox and not IE.
The problem is how a browser interprets international characters. The 'official' characters used in domain names are the 26 letters of the English (Latin) alphabet, 10 numbers, and a hyphen. But with the increase in the use of the Internet worldwide, many domain names are using international characters.
For instance, the "a" character has a value of "97", but an "a" in Cyrillic has a value of 1072. So a domain name of "www.paypal.com" could be represented (inside the HTML page code) as "www.pаypаl.com". The "а" would be displayed in your browser as an "a", so the address bar would display "www.paypal.com".
All that the phisher needs to do is to build a site that looks just like PayPal's, and they can collect your login, credit card info, etc. (For an example of these fake screens, see my report on the "Dr. Pournelle PayPal Phish".)
Internet Explorer, by default, does not support international characters. So the above technique will not work for IE users. But Firefox (version 1.0, probably all) does support international characters, so it is vulnerable to this phishing attack.
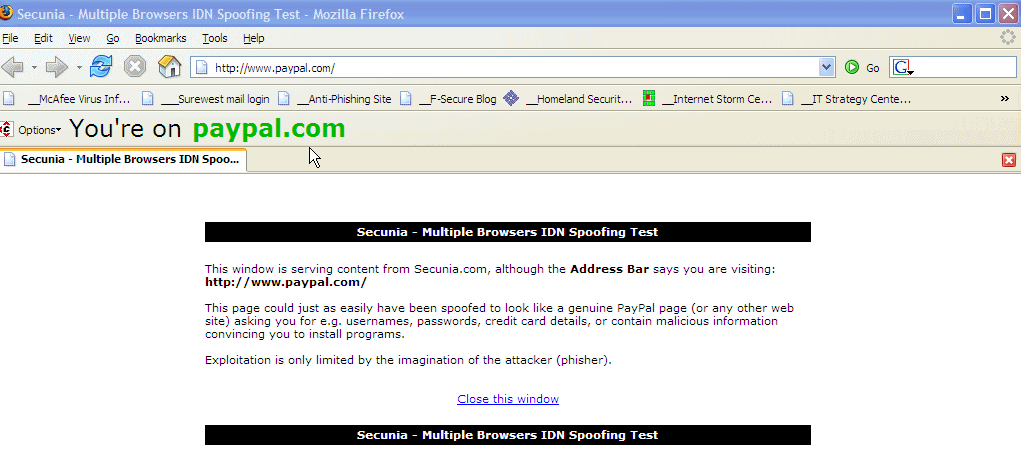
Is the browser that you are using vulnerable? Here is a link to "PayPal" -- only it's not. If your browser is vulnerable, a new window will open up and you will be at Securnia's special test page. But notice that the address bar will show a valid PayPal address. (The code underneath that link is an 'a href' to 'http://www.paypаl.com/'.) Notice that if you 'hover' your mouse over the above link, the status bar will show a 'valid' PayPal address. You can get to the full Securnia page here.
This is what Firefox (version 1.0; latest, with SpoofStick toolbar installed) will display with that Secunia's test page:

Notice that SpoofStick seems to agree that you are on the PayPal site.
Here's the same test page as rendered in IE 6 (latest version, fully patched, SpoofStick toolbar installed):
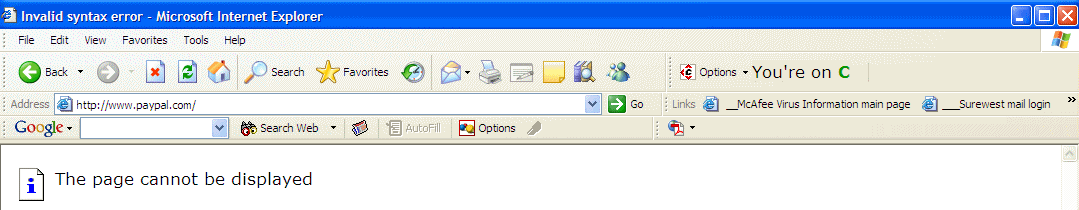
That same page when displayed with IE gives you a "Page Not Found" error, even though the address bar shows the PayPal link.
If you happen to have IE and Firefox installed, try the above link in each of the browsers to see your results.
So an interesting turn of events. After all the hand-wringing over the vulnerability of IE and Outlook to phishing attack techniques that obscure the actual URL of a link, it turns out that IE is not vulnerable to this technique, but the open-source Firefox is.
As I write this (Feb 7, 2005), Firefox is mulling over their response to this problem. And there are beginning to be more vulnerabilities found in Firefox. (Update 2/8/05: Although there is a lot of 'traffic' on the FireFox support forum, including a manual workaround that involves a manual change to a FireFox configuration file.)
This is not to say that Firefox, or other open-source programs, are not a 'good thing'. It is meant to remind you that any software can have problems, and one needs to be careful.
In the meantime, there is something you can do. As noted in our 'phishing report', you can add "SpoofStick" to your browser. It's available from www.spoofstick.com, and there are versions for IE or Firefox. It will display a "You're on..." banner in the toolbar area that tells you where you really are. Here's a screenshot of how it would look while browsing our "Digital Choke Daynotes" with Internet Explorer:
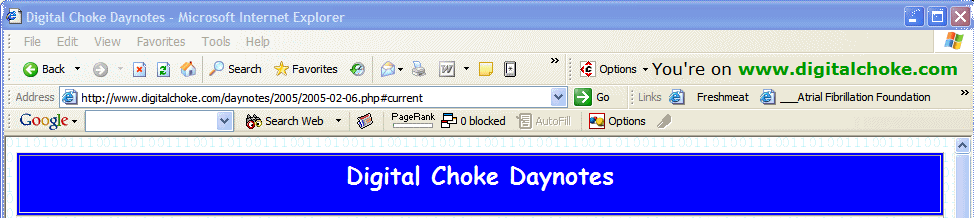
Note the "You're on .." section in the upper right. That verifies your actual location on the 'net. (Update 2/8/05: further testing with SpoofStick and FireFox shows that SpoofStick won't help in this case, although it is helpful with other address spoofing techniques ... as you can see by the previous screen shots.)
I've been using SpoofStick for several months without problems. Recommended.
In the meantime, be careful about where you go. Stay away from the 'dark places' that ask you for your financial information. Type in the address; don't click on links in emails or web pages automatically. Get your updates for all of your software, Windows and 'open source' and applications.
As we have said before, be careful out there. Lock your doors. Take your keys. Eat your vegetables. Hug your spouse and children. Call your mother.
Rick Hellewell -- May 23, 2011 07:59 PM
Our main site is at http://www.digitalchoke.com
More comments available on our "Daynotes" site: http://www.digitalchoke.com/daynotes. Your are invited to send your comments or questions here.